Db2 Forum. Southwest Db2 Users Group – February 2018 – Grapevine (Dallas), TX, USA
SEGUS & SOFTWARE ENGINEERING proudly sponsor this event & present:
1 – Pdf Präsentation – Compliance with compliments! Viable Db2 z/OS workload tracking.
2 – Pdf Präsentation – Db2 12 Continuous Delivery – New challenges for deployment.
3 – Pdf Präsentation – Db2 z/OS Lies, Damn Lies, and Statistics…
1 – Db2 z/OS Security Audit: Compliance with compliments! Viable Db2 z/OS workload tracking.
Audit and Compliance is a need that many companies want and have to fulfill.
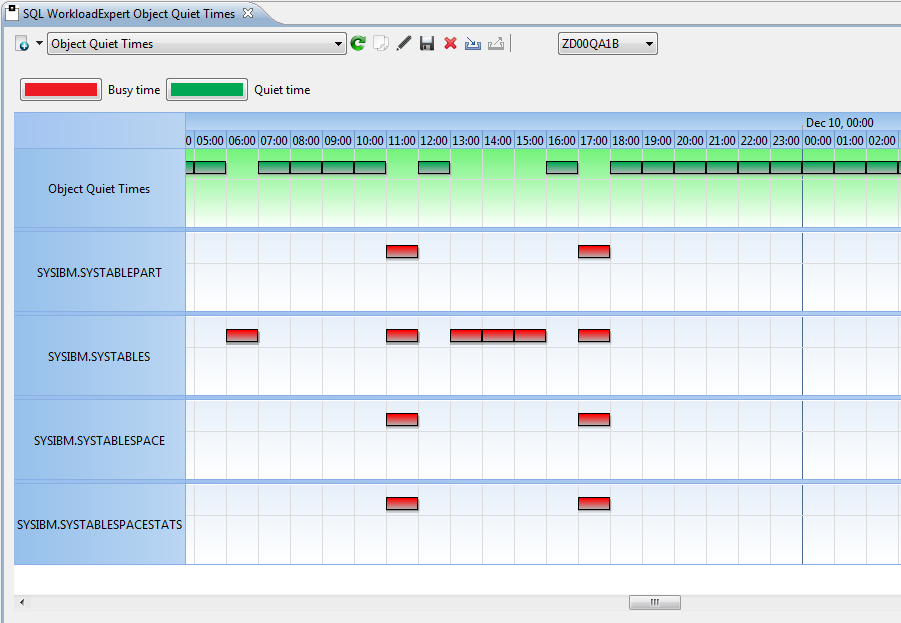
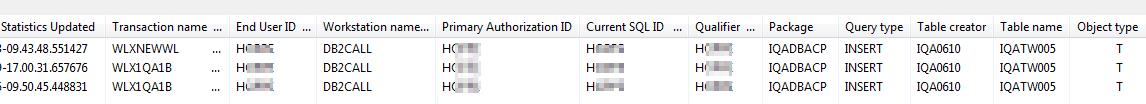
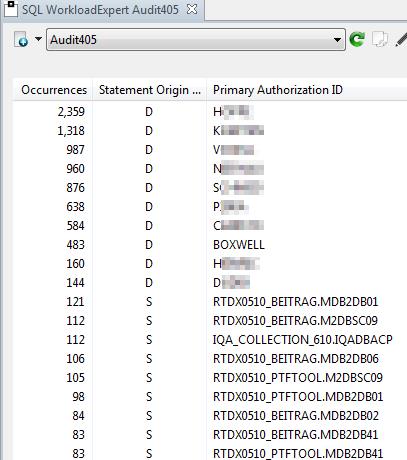
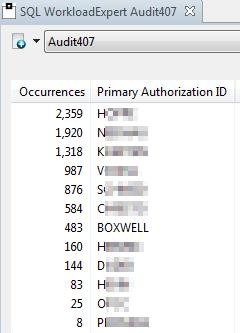
There’s different ways and tools that promise to be able to do it, but what can they really do and what are the associated costs? This presentation introduces Db2 10/11 technology exploitation that delivers any DML, DDL, DCL being executed in a Db2 environment along with identification details. Learn how you can run Audit analytics against a long‐term repository, pinpointing who executed a query, when and from where. Analyze your entire workload to understand access patterns and abnormalities.
More about Db2 Audit
Presentation Outline
- Audit needs and musts Take a journey to GLB HIPAA PCI‐DSS Basel III Sarbanes‐Oxley CA SB1386 Federal Information Security Management Act “ed Flag”Rules (FRCA)5.
- Solution overview and their Pros/Cons Get an overview about the existing solutions and understand how they work.
- The viable way – let Db2 do the magic! Learn about Db2 enhancements in Db2 10/11 that deliver the Db2 workload being processed and understand why it’s so efficient.
- Customer results from the banking industry Receive some experience from a large banking company and how they successfully replaced their Db2 Audit feature based reporting by a modern SQL tracking and analytics process.
2 – Db2 12 Continuous Delivery – New challenges for deployment.
Fundamental changes in the Db2 z world often lead to concerns. Let’s face it – some changes force us to change! While a Db2 version migration usually took months, or even years, there will be no new Db2 version after 12, but continuous code drops.
This will have a tremendous impact on migration strategies, because we have to find a reliable way to test these code deliveries in a fraction of time. If we make it, Business Divisions will become enthused at how quickly new technology becomes available for new applications. This presentation will describe the difference between Code, Catalog, Function and Application Levels, how you can control them and how you can fallback in case of anomalies. It also illustrates how we still can be pro-active in testing without burning weeks and months.
Learn how to choose from four different levels of testing and a new way of automation. CD-Screening allows you to pick and choose from KPI based test automation. The levels include simple anomaly alerting, access path verification, clone Pre-apply and even workload capture/replay to easily discover different behaviour resulting from a new code Level.
More about Db2 Continuous Delivery – CD
Presentation Outline
Joining this presentation, you’ll learn how to align Continuous Delivery to your Continuous Availability.
- Agile, Continuous Delivery, DevOps – just buzz words, or new methodologies?
- Db2 Code, Catalog, Function and Application Levels – differences and dependencies.
- Activation/Deactivation of new code and how to fallback and when you can’t.
- Different flavors of (pro-active) CD-Screening and how it can be automated:
* Anomaly alerting based on Incompatibility Change Indicators (ICIs)
* Dyn./Stat.Access Path Change Detection e.g.via Plan Management
* Clone based code change pre-apply exploiting Backup System
* Workload-KPI verification using SQL replay and KPI comparison
Audience Experience: Intermediate Advanced
Platform: Db2 z/OS
Presentation Length: 60 minutes
Presentation Category: Database Administration Performance Management Db2 Migration
3 – Db2 z/OS Lies, Damn Lies, and Statistics…
– Benjamin Disraeli, Prime Minister of England (1868, 1874-1880)
The above line may, or may not, have been spoken well over 100 years ago, but the need for statistics and, above all else, accurate statistics is more important than ever in the Db2 world of today.
More about Db2 RUNSTATS
Presentation Outline
- Db2 RUNSTATS basics & catalog tables and Columns used for access path
- IBM recommendations through the ages : from Db2 V3 to Db2 12
- Db2 RUNSTATS advanced
- SYSCOLDIST explained
- RUNSTATS real world Q&A :
use of SAMPLE, COLGROUP, PROFILE, REOPT (ONCE), TABLESAMPLE SYSTEM, HISTOGRAM, … - RUNSTATS reversal
Speaker biography
Roy Boxwell has more than 32 years of experience in MVS, OS/390, and z/OS environments – 30 of those in Db2. He specializes in installation, migration, and performance monitoring and tuning. Roy leads the SEG development team responsible for the real time database maintenance solutions. He is also an active participant, speaker and contributor on the IDUG Db2 Listserv and sends out a monthly Db2 z/OS Newsletter.